UNCOVER: Development of an efficient steganalysis framework for uncovering hidden data in digital media
Steganalysis of JSteg algorithm using hypothesis testing theory – topic of research paper in Mathematics. Download scholarly article PDF and read for free on CyberLeninka open science hub.

Digital image steganography survey and investigation (goal, assessment, method, development, and dataset) - ScienceDirect
Entropy | Free Full-Text | Modern Text Hiding, Text Steganalysis, and Applications: A Comparative Analysis

Steganalysis of Very Low Embedded JPEG Image in Spatial and Transform Domain Steganographic Scheme Using SVM | SpringerLink

A comprehensive review of video steganalysis - Bouzegza - 2022 - IET Image Processing - Wiley Online Library

Steganalysis of JSteg algorithm using hypothesis testing theory | EURASIP Journal on Information Security | Full Text

Steganalysis of convolutional neural network based on neural architecture search | Multimedia Systems
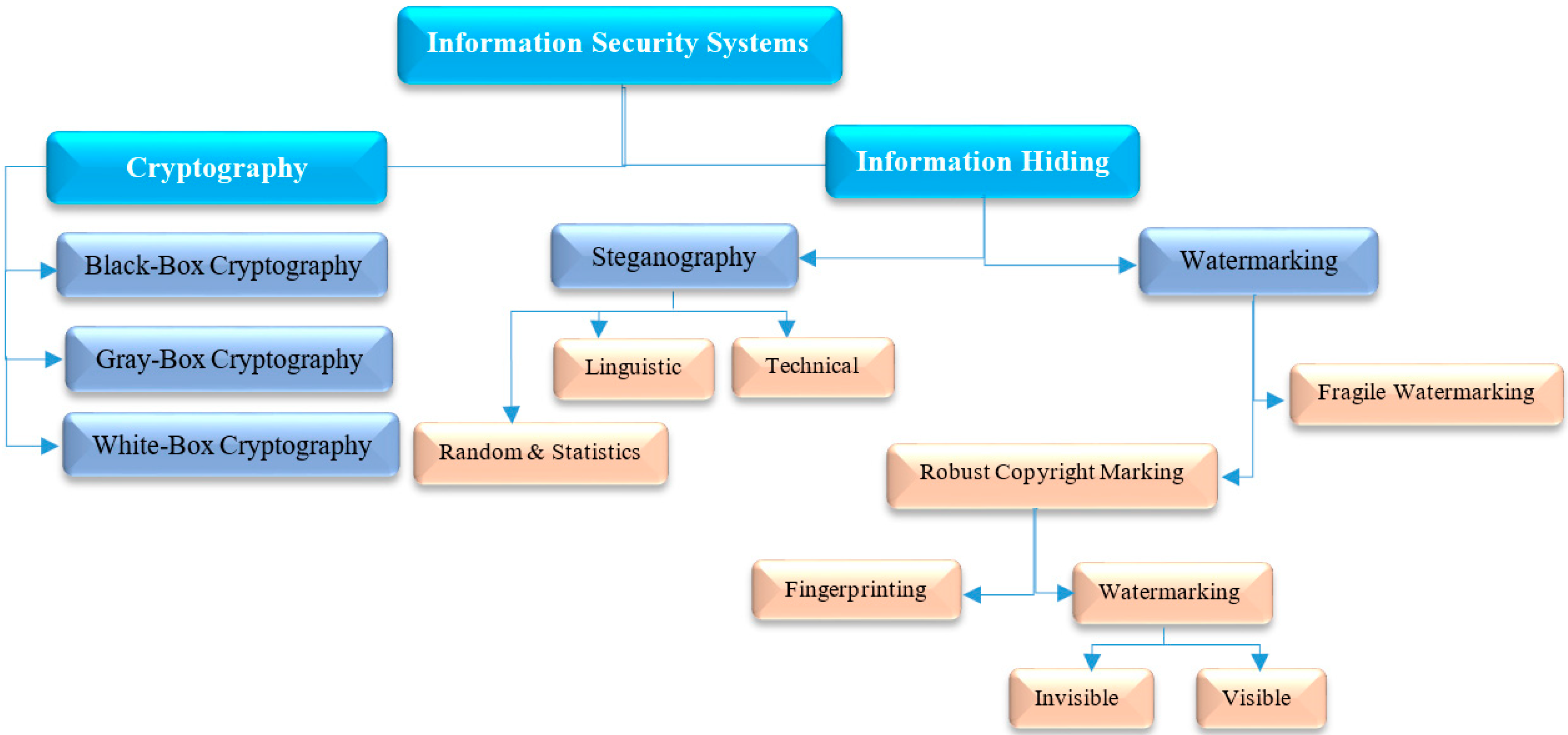
Entropy | Free Full-Text | Modern Text Hiding, Text Steganalysis, and Applications: A Comparative Analysis

Novelty Detection in Blind Steganalysis: Tom A S Pevn y Elix Viallet Jessica Fridrich | PDF | Support Vector Machine | Statistical Classification
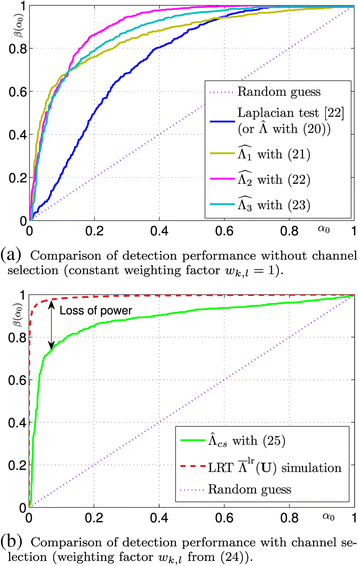
Steganalysis of JSteg algorithm using hypothesis testing theory | EURASIP Journal on Information Security | Full Text






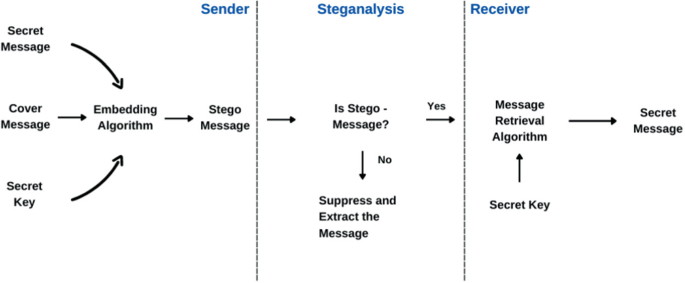


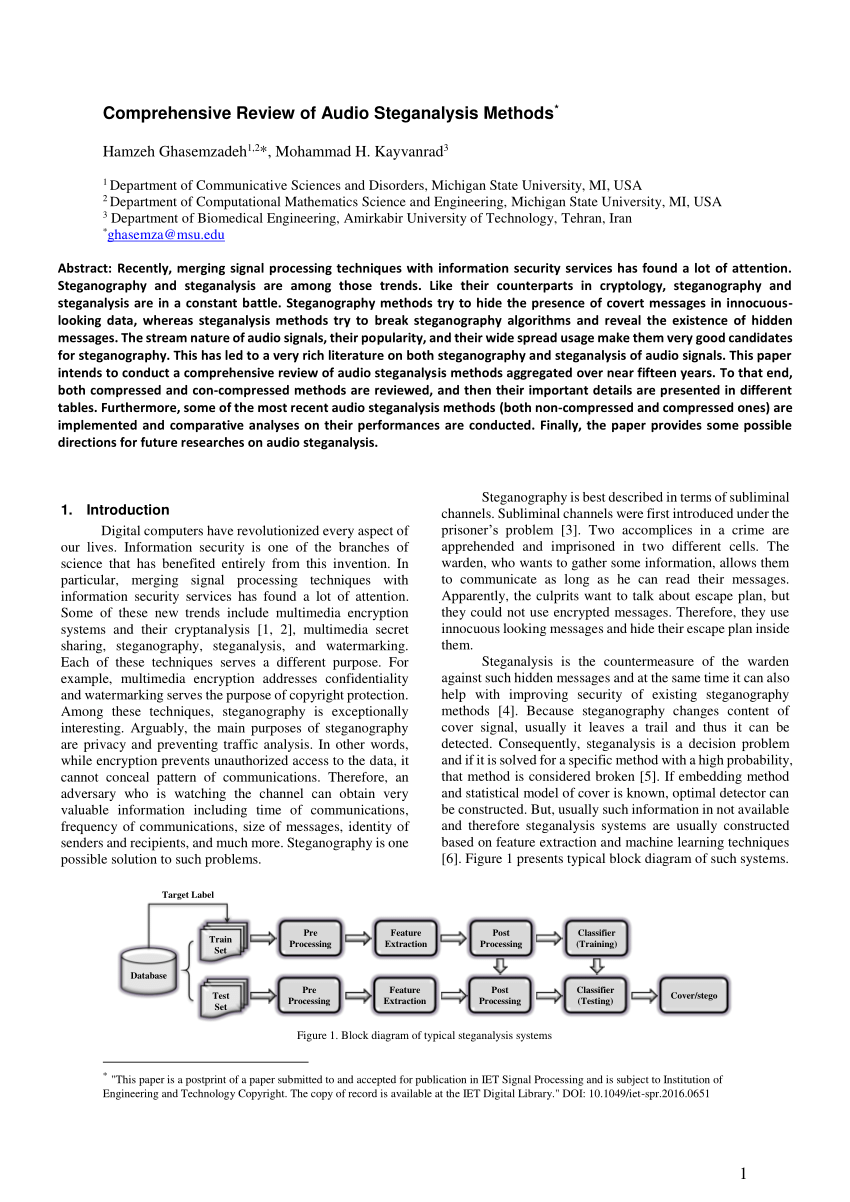
![PDF] StegoNet: Turn Deep Neural Network into a Stegomalware | Semantic Scholar PDF] StegoNet: Turn Deep Neural Network into a Stegomalware | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6c141b0c8916527fb85590331c1f0fe8b91f819e/9-Figure6-1.png)